Azure Retires Default Outbound Access for New VMs – What You Need to Know
Azure Tightens Security: Say Goodbye to Default Outbound Access for New VMs ☁️
Introduction
Heads up: Microsoft is retiring default outbound access for new Azure VMs starting September 30, 2025. If a VM is created without configuring an explicit internet connection method, it won’t be able to reach external endpoints unless you take action.
⏳ What’s Changing — And What Doesn’t
From September 30, 2025, new VMs deployed without defined outbound connectivity—like a NAT Gateway, Load Balancer outbound rule, or assigned public IP—will no longer have internet access.
However, existing VMs using default outbound access remain unaffected—they’ll keep working, though Microsoft recommends transitioning to explicit methods for long-term stability.
🔒 Why This Transition Makes Sense
- Security & Zero Trust alignment — Implicit internet access by default runs counter to modern security best practices.
- Stability & predictability — Default outbound IPs are owned by Microsoft, not you, and can shift without notice. Explicit methods give you traceable, stable IPs.
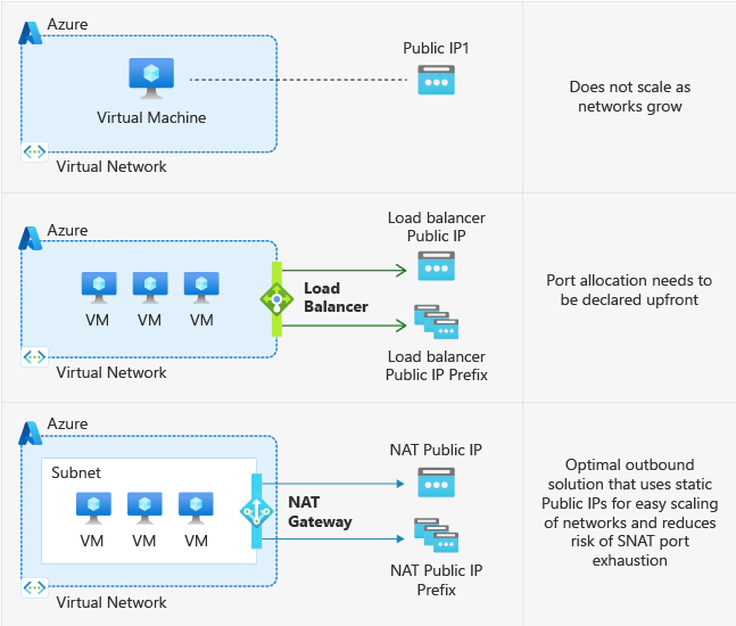
⚙️ Choose Your Outbound Strategy
| Option | Best For | Strengths |
|---|---|---|
| NAT Gateway | VMs that only need internet access (e.g., updates) | Scalable, secure, and recommended |
| Standard Load Balancer (outbound rules) | When also needing inbound access | Flexible, cost-efficient |
| Assigned Public IP | Testing environments or VMs needing unique IPs | Simple and transparent setup |
🗣 Real-World Insights from the Field
On Reddit, one Azure user commented:
“This only affects workloads using Virtual Network NAT without a PubIP/NSG assigned. … If you are not using either of these options, your workload network design is wrong.”
In other words: if you’re still relying on the implicit default, it’s time to get explicit.
🌐 VM Behavior in Shared Subnets
If existing VMs in a subnet inherited default access while new ones don’t, Azure recognizes the difference based on deployment timing, not subnet. So older VMs keep access, while new ones don’t—unless you configure explicit outbound paths.
Microsoft recommends migrating all VMs—new and old—to explicit methods to avoid confusion and increase consistency.
✅ What to Do Next
- Audit your VMs with Azure Advisor—look for the “Add explicit outbound method to disable default outbound” recommendation.
- Plan an explicit outbound strategy, choosing between NAT Gateway, Load Balancer rules, or Public IPs based on your use case.
- Prioritize security and stability—especially for production workloads, using solutions that align with compliance, traceability, and resilience goals.
📝 In Summary
- Default outbound access for new VMs ends September 30, 2025.
- Existing VMs remain functional, but planning for explicit connections is essential.
- Choose between NAT Gateway, Load Balancer, or Public IP, depending on your architecture needs.
- Audit now, adapt faster—this is your chance to modernize and secure Azure network design.
